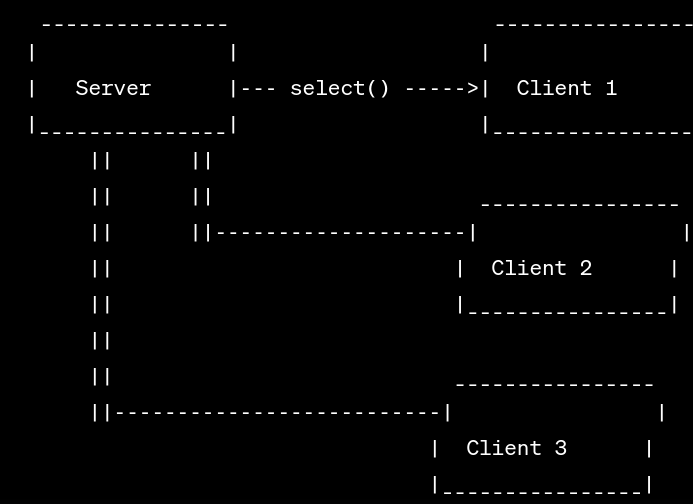
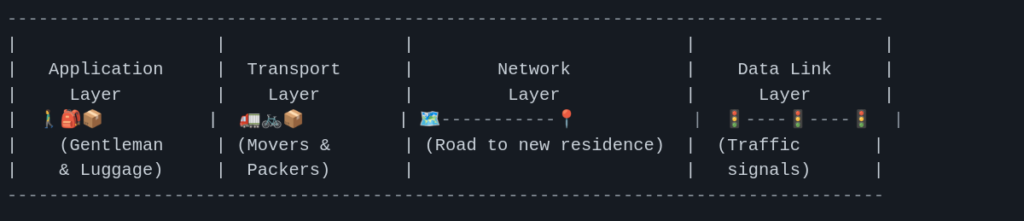
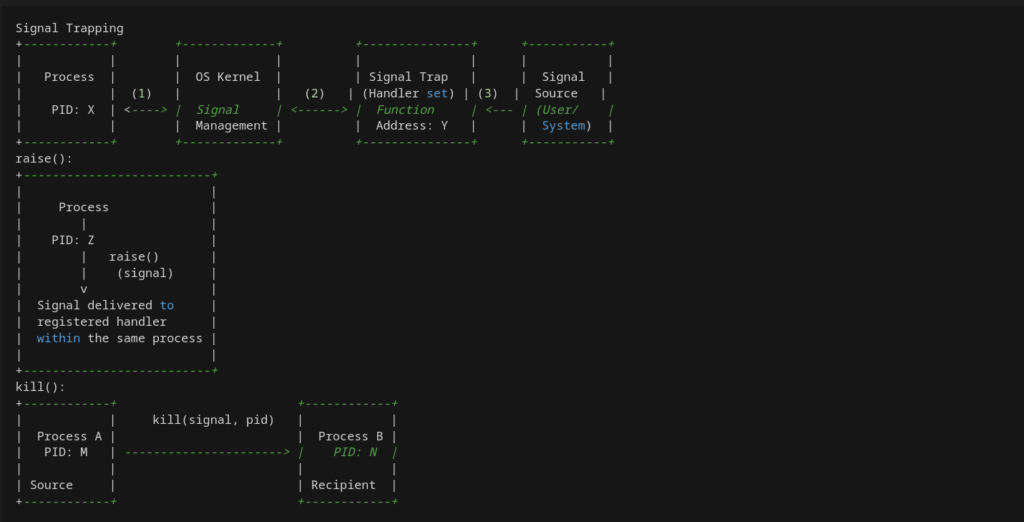
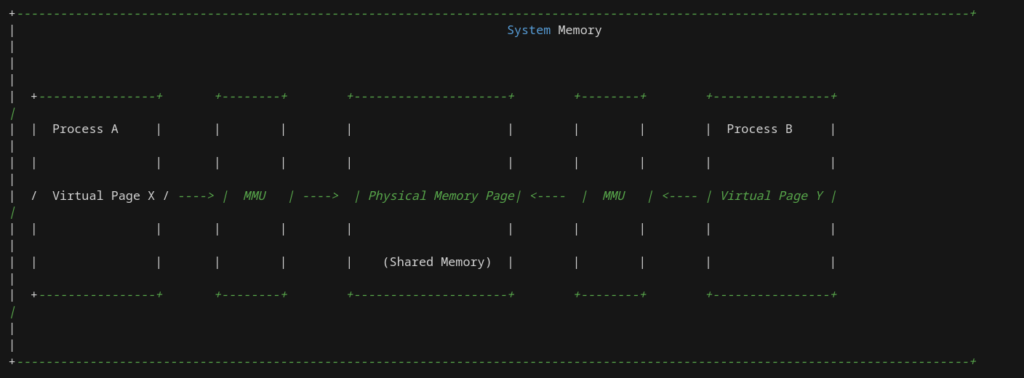
Guardian of Threads: The Semaphore Saga
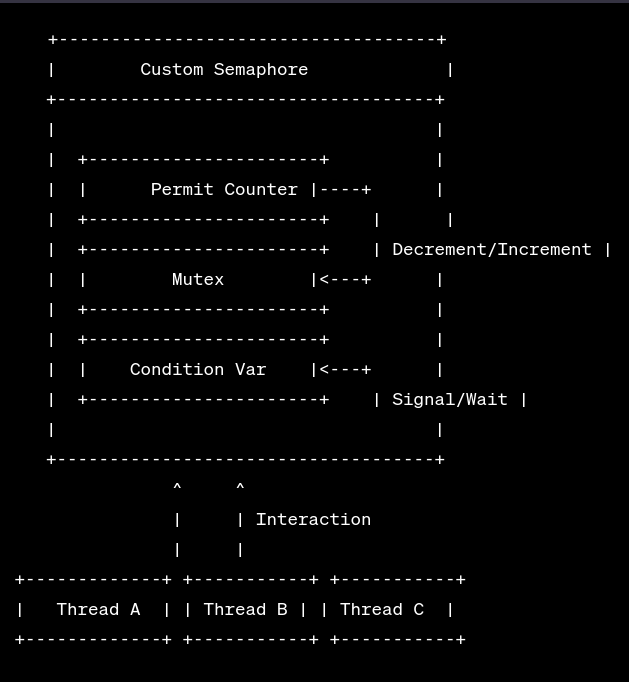
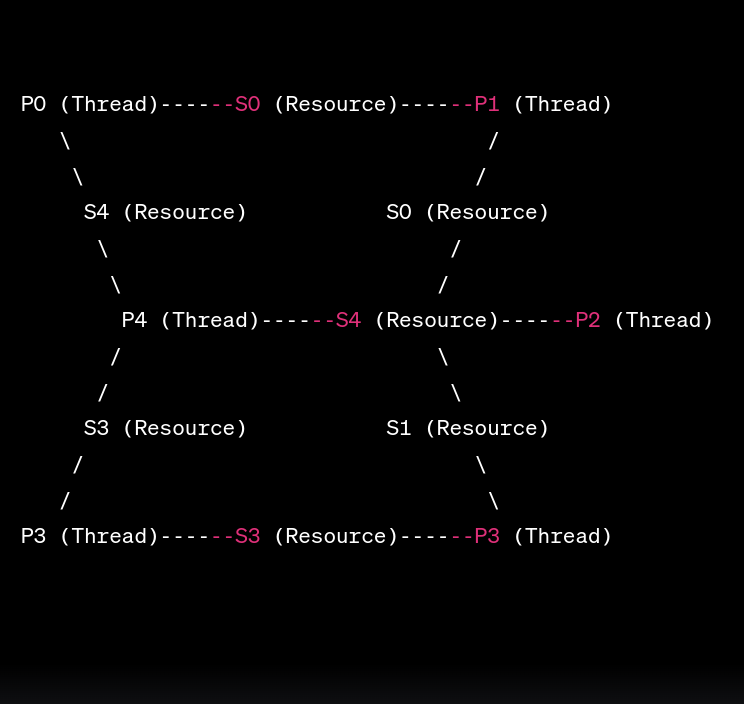
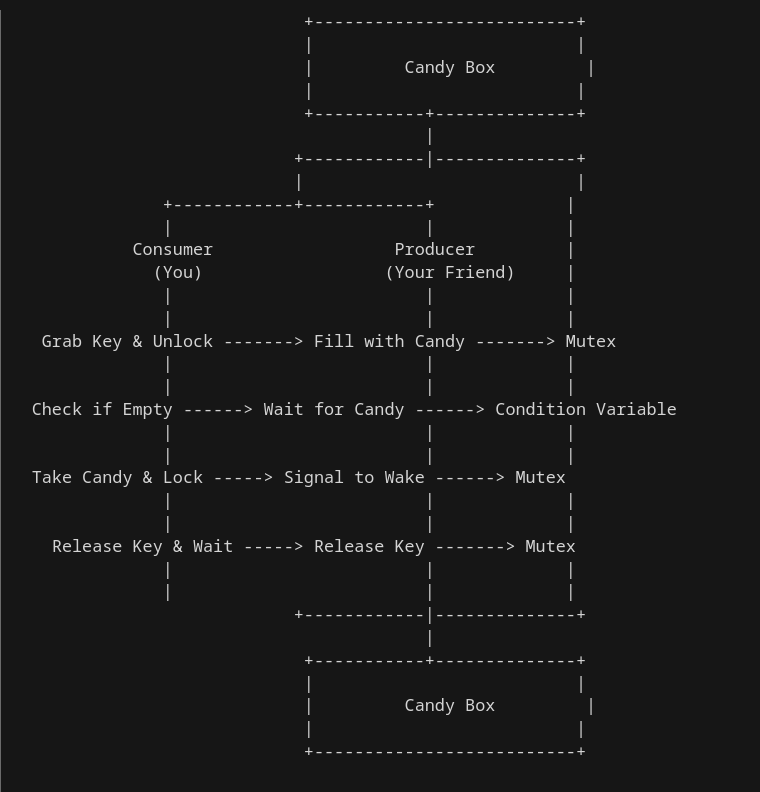
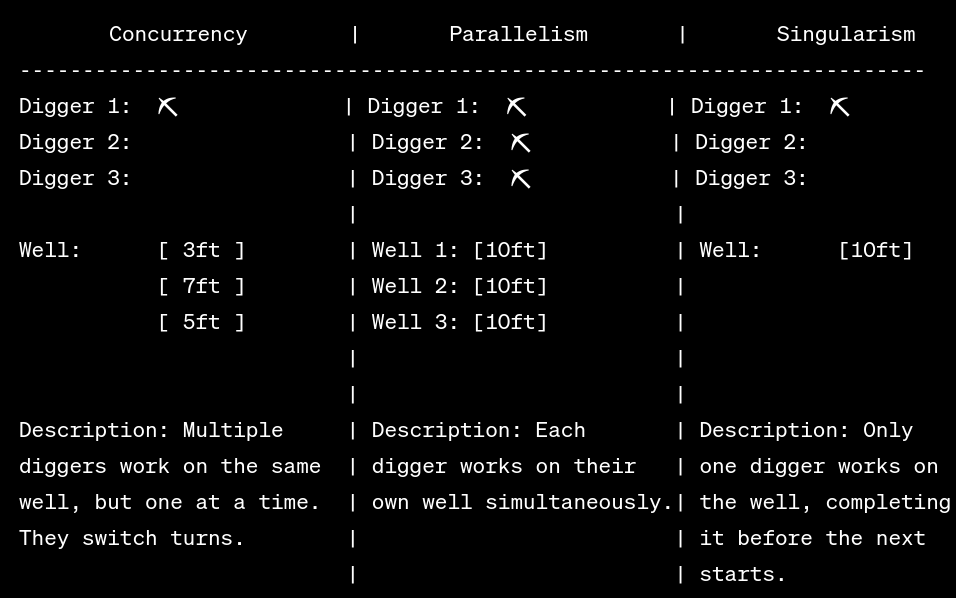
Diving Deep into Concurrency: Building My Own Semaphore in C! 💻🔥 Hey tech enthusiasts! 🚀 Concurrency and multi-threading are the realms where computer science gets intriguingly complex. Today, I’m super excited to unravel a project where I ventured into creating my very own semaphores in C! 🧩 For the uninitiated, semaphores are these …